This entry is a post in a series in order to identify Tor (the onion router) network traffic and usage using Bro Network Security Monitor. To learn more about both projects, please visit the aforementioned links. This post is not to argue the merits of allowing Tor to run on a network. Due to malware variants taking advantage of Tor for its botnet command and control (C2), I wanted to be able to effectively identify Tor usage in hopes of identifying hosts that may be using Tor for C2 purposes.
A method folks often use to identify communication with Tor relays is to compare the current list of known Tor servers with the traffic from their network. While this does work, some relays may host other legitimate services which could introduce false-positives. The goal was to find a method to augment the parsing network traffic for Tor server matches which is sometimes done retrospectively.
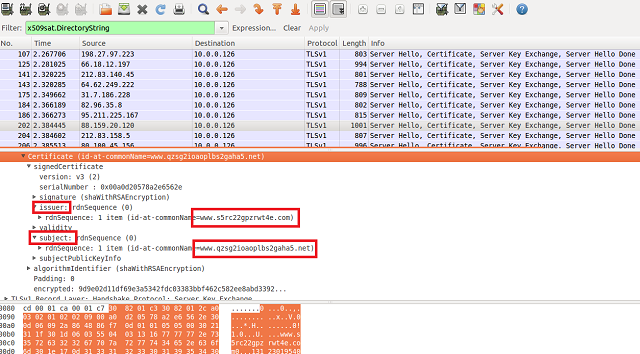
If we take a look at the Tor certificates, we see an interesting pattern for the Issuer and Subject ID form a pattern.
Using tshark, it the Issuer and Subject ID patterns are a little more apparent.
$ tshark -r tor.pcap -T fields -R "ssl.handshake.certificate" -e x509af.utcTime -e x509sat.uTF8String
13-10-15 00:00:00 (UTC),14-02-11 23:59:59 (UTC) www.axslhtfqq.com,www.hkkch64skp7am.net
13-12-30 18:32:48 (UTC),14-12-30 18:32:48 (UTC) www.igdpzct5tauwgyqs.com,www.4tdznzbrfuv.net
13-10-04 00:00:00 (UTC),14-04-22 00:00:00 (UTC) www.3pxivyds.com,www.nolspqtib3ix.net
13-11-17 00:00:00 (UTC),14-06-22 00:00:00 (UTC) www.3pzqe4en5.com,www.glk3fwiz6.net
13-06-19 00:00:00 (UTC),14-04-20 00:00:00 (UTC) www.5orbut4ufhohm5rlj47.com,www.orutxjqwf.net
13-06-15 00:00:00 (UTC),14-02-04 00:00:00 (UTC) www.7wdf4rkj5mew.com,www.sd5mkmsmo.net
13-11-19 00:00:00 (UTC),14-02-05 23:59:59 (UTC) www.75ba5lymxpbhw3a2kb.com,www.rnspic4yus5crf6w.net
13-12-30 19:54:02 (UTC),14-12-30 19:54:02 (UTC) www.s5rc22gpzrwt4e.com,www.qzsg2ioaoplbs2gaha5.net
13-08-12 00:00:00 (UTC),14-04-16 23:59:59 (UTC) www.2fwld67ac2.com,www.6suxdq3miwwewq4.net
13-12-18 00:00:00 (UTC),14-02-14 23:59:59 (UTC) www.npmxal2ohuefme26yf.com,www.c7kriuquvh.net
13-10-18 00:00:00 (UTC),14-06-16 00:00:00 (UTC) www.s426lumoi7.com,www.ouzbot23a6lw3vvmszx.net
13-12-31 00:00:00 (UTC),14-02-01 23:59:59 (UTC) www.vywbff5wkza6npkd5l.com,www.ugdrrog5ro5wdfddj.net
13-11-27 00:00:00 (UTC),14-08-13 00:00:00 (UTC) www.ozsx22b4nda.com,www.lr7s5k3n6ber.net
13-03-31 00:00:00 (UTC),14-01-06 23:59:59 (UTC) www.plgx26wgyroot37x3ysj.com,www.xwx5gpj5t2msq3.net
13-12-18 00:00:00 (UTC),14-02-20 00:00:00 (UTC) www.gempmzrnwnk.com,www.6lrz7wtwprz.net
13-08-16 00:00:00 (UTC),14-01-26 23:59:59 (UTC) www.rxy4jiw4wk.com,www.g66mipkcyhjwumywk4h.net
13-12-30 19:07:41 (UTC),14-12-30 19:07:41 (UTC) www.o5qzqtbs.com,www.bnymkm3nk7jtz3.net
13-07-27 00:00:00 (UTC),14-01-18 00:00:00 (UTC) www.rtqtkopfct767ai.com,www.facp2b2y5wjffbo5ioy.net
13-09-09 00:00:00 (UTC),14-02-26 00:00:00 (UTC) www.lvv4l6sx3qafei2s5u.com,www.vznlngjz7a2fpg.net
13-12-21 00:00:00 (UTC),14-02-08 00:00:00 (UTC) www.mbrdx4tz2ob5wlvazlr.com,www.shxl35n3zt.net
13-12-12 00:00:00 (UTC),14-01-15 00:00:00 (UTC) www.4jvdpoo5wcklhd3usu.com,www.f4uxyorx2h.net
13-10-17 00:00:00 (UTC),14-05-05 00:00:00 (UTC) www.zcgg5yiwzajal4.com,www.55a4kx5jrqxezvk.net
13-05-18 00:00:00 (UTC),14-04-07 23:59:59 (UTC) www.3eexfeaw.com,www.iedhzej4tie4egm.net
13-12-23 00:00:00 (UTC),14-01-22 23:59:59 (UTC) www.5m6ywj2w7zs.com,www.iolbr3jbfs.net
13-03-09 00:00:00 (UTC),14-01-01 23:59:59 (UTC) www.hbwpqbx4zimtptui.com,www.77wneeix55t.net
13-12-26 00:00:00 (UTC),14-04-19 00:00:00 (UTC) www.pxznjv3t75.com,www.wuqq77l634eogfm.net
13-12-07 00:00:00 (UTC),14-03-17 23:59:59 (UTC) www.6pp7bfbdywvcaicqmfq.com,www.g6oa3qdobmdgl5tprm.net
13-12-30 19:42:49 (UTC),14-12-30 19:42:49 (UTC) www.twngp3xrqgo4p.com,www.znskvp5k5pns22y2.net
13-02-14 00:00:00 (UTC),14-01-14 00:00:00 (UTC) www.spx5a4e5eyhkdtpt2xj.com,www.6phyovjhggkfm.net
So with this knowledge I started looking to see if there were any current methods of identifying the anomalous certificate identifiers. Lucky for Bro users, Seth Hall created a detect-tor.bro script to do just that. I downloaded the latest Bro 2.4 source package and built it on my Ubuntu VM. I also pulled down the aforementioned detect-tor.bro script. I was greeted with a warning and did not see the expected logs:
$ sudo /usr/local/bro/bin/bro -r tor.pcap detect-tor.bro
warning in /usr/local/bro/share/bro/base/misc/find-checksum-offloading.bro, line 54: Your trace file likely has invalid TCP checksums, most likely from NIC checksum offloading. By default, packets with invalid checksums are discarded by Bro unless using the -C command-line option or toggling the 'ignore_checksums' variable. Alternatively, disable checksum offloading by the network adapter to ensure Bro analyzes the actual checksums that are transmitted.
This was quickly fixed by including the -C toggle in order to ignore checksums.
$ sudo /usr/local/bro/bin/bro -C -r tor.pcap detect-tor.bro
After parsing the Tor traffic collected via Wireshark or tcpdump, Bro should have generated some logs. At first glace, we see an alert from the detect-tor.bro script. While the event is pretty self explanatory, note the destination IP addresses are not included because Tor will usually have multiple servers, i.e. destination IP addresses.
$ more notice.log
#separator \x09
#set_separator ,
#empty_field (empty)
#unset_field -
#path notice
#open 2014-01-03-14-12-05
#fields ts uid id.orig_h id.orig_p id.resp_h id.resp_p fuid file_mime_type file_desc proto note msg sub src dst p n peer_descr actions suppress_for dropped remote_location.country_code remote_location.region remote_location.city remote_locatio
n.latitude remote_location.longitude
#types time string addr port addr port string string string enum enum string string addr addr port count string table[enum] interval bool string string string double double
1388434821.597322 - - - - - - - - - DetectTor::Found 10.0.0.126 was found using Tor by connecting t
o servers with at least 10 unique weird certs - 10.0.0.126 - - - bro Notice::ACTION_LOG 3600.000000 F - - -- -
#close 2014-01-03-14-12-05
We can cut down column noise by specifying only what we want to see:
$ cat notice.log|/usr/local/bro/bin/bro-cut -c -d note msg src dst actions suppress_for dropped
#separator \x09
#set_separator ,
#empty_field (empty)
#unset_field -
#path notice
#open 2014-01-03-14-12-05
#fields note msg src dst actions suppress_for dropped
#types string string addr addr table[enum] interval bool
DetectTor::Found 10.0.0.126 was found using Tor by connecting to servers with at least 10 unique weird certs 10.0.0.126 - Notice::ACTION_LOG 3600.000000 F
After seeing the alert in the notice.log, we look in the ssl.log file as well in order to determine what traffic caused the alert to fire.
$ more ssl.log
#separator \x09
#set_separator ,
#empty_field (empty)
#unset_field -
#path ssl
#open 2014-01-03-14-12-05
#fields ts uid id.orig_h id.orig_p id.resp_h id.resp_p version cipher server_name session_id subject issuer_subject not_va
lid_before not_valid_after last_alert client_subject client_issuer_subject
#types time string addr port addr port string string string string string string time time string string string
1388434821.514935 CwRHlF31djcMrO7Z98 10.0.0.126 51191 199.36.221.196 9001 TLSv10 TLS_DHE_RSA_WITH_AES_256_CBC_SHA www.wplgkqpnteb.com -CN=www.ri6ufvqioii5se5tzbgt.net CN=www.dyyp6enzivlm46.com 1388447336.000000 1419983336.000000 - - -
1388434821.482053 Ck1Mgy4ubChMFyneFc 10.0.0.126 38946 198.27.97.223 443 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.p65b.com - CN=www.hkkch64skp7am.net CN=www.axslhtfqq.com 1381809600.000000 1392181199.000000 - - -
1388434821.533291 CZOEio3mxlQgpmVD2i 10.0.0.126 36715 149.9.0.60 9001 TLSv10 TLS_DHE_RSA_WITH_AES_256_CBC_SHA www.dpvdl3n6yzwv.com -CN=www.anojueopqlpgsj.net CN=www.u2rsltgpogir6t.com 1384405200.000000 1398830399.000000 - - -
1388434821.484476 CnU0VyJcJHaeCaxh8 10.0.0.126 49341 66.18.12.197 443 TLSv10 TLS_DHE_RSA_WITH_AES_256_CBC_SHA www.6kyx72vjlrwxcmxnj4
we7n.com - CN=www.4tdznzbrfuv.net CN=www.igdpzct5tauwgyqs.com 1388446368.000000 1419982368.000000 - - -
1388434821.484255 Cc00yR3kKWb2GstwXf 10.0.0.126 40742 64.62.249.222 443 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.de5v2whiex3xxy.com
- CN=www.glk3fwiz6.net CN=www.3pzqe4en5.com 1384664400.000000 1403409600.000000 - - -
1388434821.583284 CuVFNK14saFKjGVhfh 10.0.0.126 54393 50.115.122.68 9001 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.ojj4rbje7z7.com -CN=www.qexiojanju56.net CN=www.nnfslkrseh.com 1387342800.000000 1390280400.000000 - - -
1388434821.482585 CROLl5Vd0jUzvvwn 10.0.0.126 46797 212.83.140.45 443 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.esd7jqvwpbwebf.com
- CN=www.nolspqtib3ix.net CN=www.3pxivyds.com 1380859200.000000 1398139200.000000 - - -
1388434821.597288 CXemGQ4G0PFf5DvUf 10.0.0.126 34887 72.52.91.30 5901 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.igyewbs5.com -CN=www.bnlln35al.net CN=www.henq76fjat2ozl2537.com 1376020800.000000 1403841600.000000 - - -
1388434821.597322 CFrNiH22BOLl917zjl 10.0.0.126 56135 144.76.109.178 9081 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.57xl.com - CN=www.3rvuayihf4t35h.net CN=www.viw7rvktu36ov.com 1386651600.000000 1388811600.000000 - - -
1388434821.489984 CxEp7Xmn9AOlkxn0e 10.0.0.126 44997 31.7.186.228 443 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.ewrk2xtmr.com -CN=www.orutxjqwf.net CN=www.5orbut4ufhohm5rlj47.com 1371614400.000000 1397966400.000000 - - -
Again, we can select the fields we want to see in order to minimize output.
$ cat ssl.log|/usr/local/bro/bin/bro-cut -c -d ts uid id.orig_h id.orig_p id.resp_h id.resp_p version cipher server_name subject issuer_subject not_valid_before not_valid_after
#separator \x09
#set_separator ,
#empty_field (empty)
#unset_field -
#path ssl
#open 2014-01-03-14-12-05
#fields ts uid id.orig_h id.orig_p id.resp_h id.resp_p version cipher server_name subject issuer_subject not_valid_before not_valid_after
#types string string addr port addr port string string string string string time string
2013-12-30T15:20:21-0500 CwRHlF31djcMrO7Z98 10.0.0.126 51191 199.36.221.196 9001 TLSv10 TLS_DHE_RSA_WITH_AES_256_CBC_SHA www.wplgkqpnteb.com CN=www.ri6ufvqioii5se5tzbgt.net CN=www.dyyp6enzivlm46.com 2013-12-30T18:48:56-0500 2014-12-30T18:48:56-0500
2013-12-30T15:20:21-0500 Ck1Mgy4ubChMFyneFc 10.0.0.126 38946 198.27.97.223 443 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.p65b.com CN=www.hkkch64skp7am.net CN=www.axslhtfqq.com 2013-10-15T00:00:00-0400 2014-02-11T23:59:59-0500
2013-12-30T15:20:21-0500 CZOEio3mxlQgpmVD2i 10.0.0.126 36715 149.9.0.60 9001 TLSv10 TLS_DHE_RSA_WITH_AES_256_CBC_SHA www.dpvdl3n6yzwv.com CN=www.anojueopqlpgsj.net CN=www.u2rsltgpogir6t.com 2013-11-14T00:00:00-0500 2014-04-29T23:59:59-0400
2013-12-30T15:20:21-0500 CnU0VyJcJHaeCaxh8 10.0.0.126 49341 66.18.12.197 443 TLSv10 TLS_DHE_RSA_WITH_AES_256_CBC_SHA www.6kyx72vjlrwxcmxnj4we7n.com CN=www.4tdznzbrfuv.net CN=www.igdpzct5tauwgyqs.com 2013-12-30T18:32:48-0500 2014-12-30T18:32:48-0500
2013-12-30T15:20:21-0500 Cc00yR3kKWb2GstwXf 10.0.0.126 40742 64.62.249.222 443 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.de5v2whiex3xxy.com CN=www.glk3fwiz6.net CN=www.3pzqe4en5.com 2013-11-17T00:00:00-0500 2014-06-22T00:00:00-0400
2013-12-30T15:20:21-0500 CuVFNK14saFKjGVhfh 10.0.0.126 54393 50.115.122.68 9001 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.ojj4rbje7z7.com CN=www.qexiojanju56.net CN=www.nnfslkrseh.com 2013-12-18T00:00:00-0500 2014-01-21T00:00:00-0500
2013-12-30T15:20:21-0500 CROLl5Vd0jUzvvwn 10.0.0.126 46797 212.83.140.45 443 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.esd7jqvwpbwebf.com CN=www.nolspqtib3ix.net CN=www.3pxivyds.com 2013-10-04T00:00:00-0400 2014-04-22T00:00:00-0400
2013-12-30T15:20:21-0500 CXemGQ4G0PFf5DvUf 10.0.0.126 34887 72.52.91.30 5901 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.igyewbs5.com CN=www.bnlln35al.net CN=www.henq76fjat2ozl2537.com 2013-08-09T00:00:00-0400 2014-06-27T00:00:00-0400
2013-12-30T15:20:21-0500 CFrNiH22BOLl917zjl 10.0.0.126 56135 144.76.109.178 9081 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.57xl.com CN=www.3rvuayihf4t35h.net CN=www.viw7rvktu36ov.com 2013-12-10T00:00:00-0500 2014-01-04T00:00:00-0500
2013-12-30T15:20:21-0500 CxEp7Xmn9AOlkxn0e 10.0.0.126 44997 31.7.186.228 443 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.ewrk2xtmr.com CN=www.orutxjqwf.net CN=www.5orbut4ufhohm5rlj47.com 2013-06-19T00:00:00-0400 2014-04-20T00:00:00-0400
2013-12-30T15:20:21-0500 CwzpD92UikR0USUErj 10.0.0.126 58912 91.121.113.70 9001 TLSv10 TLS_DHE_RSA_WITH_AES_256_CBC_SHA www.dv2nzruzkuf2ncqzpxh5vpg.com CN=www.an2nldahkafrkz6qx.net CN=www.ejybbncghc3qjraztwpr.com 2013-12-30T19:35:37-0500 2014-12-30T19:35:37-0500
2013-12-30T15:20:21-0500 CqAdrg1JryZY3kTrZ5 10.0.0.126 46649 5.135.187.167 9001 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.3h2eyn3jwsjkggg3.com CN=www.mt5unawhy.net CN=www.nexscb2bdms.com 2013-12-16T00:00:00-0500 2014-01-10T23:59:59-0500
2013-12-30T15:20:21-0500 CWYgR82bEI9IjcHp7a 10.0.0.126 37960 212.83.158.5 443 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.w5wtl.comCN=www.6suxdq3miwwewq4.net CN=www.2fwld67ac2.com 2013-08-12T00:00:00-0400 2014-04-16T23:59:59-0400
2013-12-30T15:20:21-0500 CpGUEo3d5jBpzI6L04 10.0.0.126 50935 212.83.158.50 443 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.lm6zdbm5w2jd5wxtmsfpkn.com CN=www.ouzbot23a6lw3vvmszx.net CN=www.s426lumoi7.com 2013-10-18T00:00:00-0400 2014-06-16T00:00:00-0400
2013-12-30T15:20:21-0500 CYocU22O3RREM4dfnl 10.0.0.126 49609 88.159.20.120 443 TLSv10 TLS_DHE_RSA_WITH_AES_256_CBC_SHA www.exr2poqlv774jn4ddyvf5vvv.com CN=www.qzsg2ioaoplbs2gaha5.net CN=www.s5rc22gpzrwt4e.com 2013-12-30T19:54:02-0500 2014-12-30T19:54:02-0500
2013-12-30T15:20:21-0500 CxG1gw2N7G5uvDpiD2 10.0.0.126 57656 95.211.225.167 443 TLSv10 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA www.mwqdszwnojnepwmw4souyw.com CN=www.rnspic4yus5crf6w.net CN=www.75ba5lymxpbhw3a2kb.com 2013-11-19T00:00:00-0500 2014-02-05T23:59:59-0500
2013-12-30T15:20:21-0500 CcVZHF3a5TkT9byG2e 10.0.0.126 60680 80.100.45.156 443 TLSv10 TLS_DHE_RSA_WITH_AES_128_CBC_SHA www.emqfcc55o7a4u4ecq3w63.com CN=www.c7kriuquvh.net CN=www.npmxal2ohuefme26yf.com 2013-12-18T00:00:00-0500 2014-02-14T23:59:59-0500
Pretty straight forward process to identify Tor usage on a network. This could be coupled with matching the destination addresses with the Tor server list available servers or here in order to provide further validation of Tor traffic.
Comments
comments powered by Disqus